
The importance of algorithms in our lives today cannot be overstated. They are used virtually everywhere, from financial institutions to dating sites. But some algorithms shape and control our world more than others — and these ten are the most significant.
Just a quick refresher before we get started. Though there's no formal definition, computer scientists describe algorithms as a set of rules that define a sequence of operations. They're a series of instructions that tell a computer how it's supposed to solve a problem or achieve a certain goal. A good way to think of algorithms is by visualizing a flowchart.
1. Google Search
There was a time not too long ago when search engines battled it out for Internet supremacy. But along came Google and its innovative PageRank algorithm.

Today, Google accounts for 66.7% of the U.S. market share in core search, followed by Microsoft (18.1%), Yahoo (11.2%), Ask (2.6%), and AOL (1.4%). Google now dominates the market to the point where we don't even question it anymore; for many of us, it's our primary avenue of entry into the Internet.
PageRank works in conjunction with automated programs called spiders or crawlers, and a large index of keywords and their locations. The algorithm works by evaluating the number and quality of links to a page to get a rough estimate of how important the website is. The basic idea is that the more important or worthwhile websites are likely to receive more links from other websites. It's basically a popularity contest. In addition to this, the PageRank algorithm considers the frequency and location of keywords within a web page and how long the web page has existed.
2. Facebook's News Feed
As much as we may be loathe to admit it, the Facebook News Feed is where many of us love to waste our time. And unless your preferences are set show all the activities and updates of all your friends in chronological order, you're viewing a pre-determined selection of items that Facebook's algorithms have chosen just for you.
To calculate which content is most interesting, it considers several factors, such as the number of comments, who posted the story (yes, there's an internal ranking of "popular" people and those with whom you interact with the most), and what type of post it is (e.g. photo, video, status, update, etc.).
3. OKCupid Date Matching
Online dating is now a $2 billion industry. Thanks to the growth of such sites as Match.com, eHarmony, and OKCupid, the industry has expanded at 3.5% a year since 2008. Analysts expect this acceleration to continue over the next five years — and for good reason: It's an extremely effective way for couples to meet. Not only do dating sites result in more successful marriages, they do an excellent job matching prospective couples based on their various preferences and tendencies. And of course, all this matching is done by algorithms.

Take OKCupid, for example, a free online dating site co-founded by Harvard mathematician Christian Rudder. OKCupid takes a decidedly analytic approach to online dating, pulling reams of information from their users. But there's more to OKCupid's matching algorithm than just a brute matching of common interests; each answer is weighed by how important the question is to the user and their prospective partner. It's the so-called difference that makes the difference — one that makes OKCupid one of the more effective online dating sites.
4. NSA Data Collection, Interpretation, and Encryption
We are increasingly being watched not by people, but by algorithms. Thanks to Edward Snowden, we know that the National Security Agency (NSA) and its international partners have been spying on millions upon millions of unsuspecting citizens. Leaked documents have revealed the existence of numerous surveillance programs jointly operated by the Five Eyes, an intelligence alliance comprised of the U.S., Australia, Canada, New Zealand, and the United Kingdom. Together, they've been monitoring our phone calls, emails, webcam images, and geographical locations. And by "they" I mean their algorithms; there is far too much data for humans to collect and interpret.

(ReKognition)
Interestingly, the NSA claims that they're not actually "collecting" our data. According to a 1982 procedures manual, "information shall be considered as 'collected' only when it has been received for use by an employee of a DoD intelligence component in the course of his official duties." And "data acquired by electronic means is 'collected' only when it has been processed into intelligible form." Bruce Schneier from The Guardian explains:
So, think of that friend of yours who has thousands of books in his house. According to the NSA, he's not actually "collecting" books. He's doing something else with them, and the only books he can claim to have "collected" are the ones he's actually read.
Which is a problem because:
Computer algorithms are intimately tied to people. And when we think of computer algorithms surveilling us or analyzing our personal data, we need to think about the people behind those algorithms. Whether or not anyone actually looks at our data, the very fact that they even could is what makes it surveillance.
Lastly and relatedly, there's also the NSA's Suite B Cryptography to consider, powerful algorithms that are used for encryption, key exchange, digital signatures, and hashing. This is what the agency uses to protect both classified and unclassified documents.
5. "You May Also Enjoy..."
Sites and services like Amazon and Netflix monitor the books we buy and the movies we stream, and suggest related items based on our habits.

Like any automated process, this ubiquitous feature of the 21st Century comes with its pros and cons. While it can be extremely helpful to receive such recommendations, they can also be spectacularly way off the mark — particularly after purchasing a children's book as a gift for your 3-year-old daughter.
Indeed, along with PageRank and Facebook's Newsfeed, these algorithms are creating a so-called filter bubble, a phenomenon in which users become separated from information that disagrees with their viewpoints — effectively isolating them in their own culture of ideological "bubbles." This could result in what Eli Pariser calls "information determinism" where our previous internet-browsing habits determine our future.
6. Google AdWords
Similar to the previous item, Google, Facebook, and other sites track your behavior, word usage, and search queries to deliver contextual advertising. Google's AdWords — which is the company's main source of revenue — is predicated on this model, while Facebook has struggled to make it work (when's the last time you clicked on an ad while in Facebook?).
7. High Frequency Stock Trading
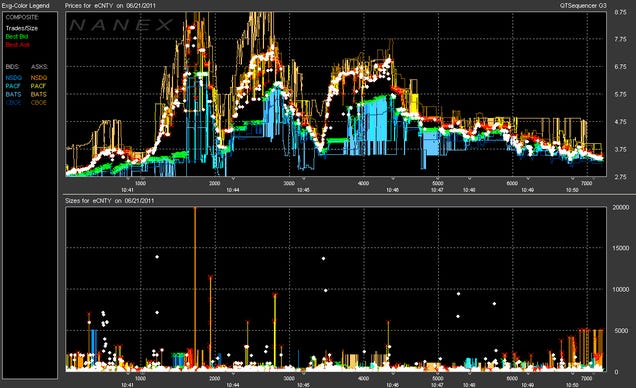
The financial sector has long used algorithms to predict market fluctuations, but they're also being used in the burgeoning practice of high-frequency stock trading. This form of rapid-fire trading involves algorithms, also called bots, that can make decisions on the order of milliseconds. By contrast, it takes a human at least one full second to both recognize and react to potential danger. Consequently, humans are progressively being left out of the trading loop — and an entirely new digital ecology is evolving.
But sometimes these algorithms make mistakes. Leo Hickman explains:
[Take] the "flash crash" of 6 May 2010, when the Dow Jones industrial average fell 1,000 points in just a few minutes, only to see the market regain itself 20 minutes later. The reasons for the sudden plummet has never been fully explained, but most financial observers blame a "race to the bottom" by the competing quantitative trading (quants) algorithms widely used to perform high-frequency trading. Scott Patterson, a Wall Street Journal reporter and author of The Quants, likens the use of algorithms on trading floors to flying a plane on autopilot. The vast majority of trades these days are performed by algorithms, but when things go wrong, as happened during the flash crash, humans can intervene.
8. MP3 Compression
Algorithms that squeeze data are an indelible and crucial aspect of the digital world. We want to receive our media quickly and we want to preserve our hard drive space. To that end, various tricks have been designed to compress and transmit data.

Back in 1991, for example, Cisco Systems developed the Compressed Real-Time Protocol (CRTP). And in 1987, researchers in Germany came up with the now-ubiquitous MP3, a compression scheme that reduces audio files to about a tenth of their original size. This compression scheme has revolutionized the music industry (for better or worse).
9. IBM's CRUSH
This one doesn't dominate our world yet, but it could very soon. An increasing number of police departments are utilizing a new technology known as predictive analysis — a tool that most certainly brings a Minority Report-like world to mind.
Back in 2010, it was announced that, by using IBM's predictive analysis software (called CRUSH, or Criminal Reduction Utilizing Statistical History), Memphis's police department reduced serious crime by more than 30%, including a 15% reduction in violent crimes since 2006. Inspired, other cities have taken notice, including those in Poland, Israel, and the UK. Pilot projects are currently underway in Los Angeles, Santa Cruz, and Charleston.
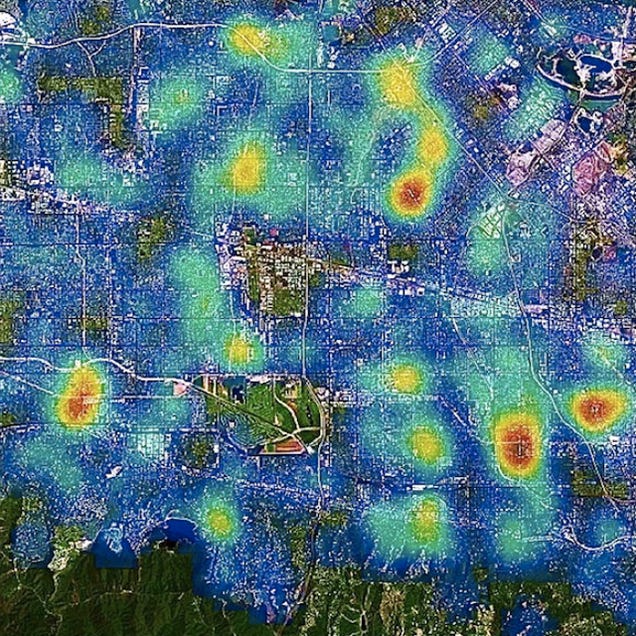
It works through a combination of data aggregation, statistical analysis, and of course, cutting-edge algorithms. It allows police to evaluate incident patterns throughout a city and forecast criminal "hot spots" to "proactively allocate resources and deploy personnel, resulting in improved force effectiveness and increased public safety."
In the future, these systems will largely take over the work of analysts. Criminals will be tracked by sophisticated algorithms that monitor internet activity, GPS, personal digital assistants, biosignatures, and all communications in real time. Unmanned aerial vehicles will increasingly be used to track potential offenders to predict intent through their body movements and other visual clues.
10. Auto-Tune
Lastly, and just for fun, the now all-too-frequent auto-tuner is driven by algorithms. These devices process a set of rules that slightly bends pitches, whether sung or performed by an instrument, to the nearest true semitone. Interestingly, it was developed by Exxon's Any Hildebrand who originally used the technology to interpret seismic data.
Cher's "Believe" is thought to be the first pop song to feature auto-tuning:
Top image: Person of Interest
Follow me on Twitter: @dvorsky

via Lifehacker http://lifehacker.com
